With the rapid development of information technology, threats to information systems are becoming increasingly sophisticated and more difficult to detect using traditional security methods. For years, organizations have relied on rule-based and signature-based attack detection to identify known threats, such as specific malware signatures, IP addresses, or triggering rules defined by security teams.

While effective at detecting known attacks and threats, rules-based systems are ineffective against new, unknown, or sophisticated attacks that don’t fit any previously identified patterns. With the rise of cloud services, remote work, and advanced persistent threats (APTs), security teams need more intelligent and adaptive approaches. One powerful solution gaining traction is anomaly detection – a method of identifying threats by detecting unusual activity, even when there are no known rules or signatures.
In this article, we’ll explore anomaly detection—what it is, how it works, the main types, practical applications, and the pros and cons of using it. Anomaly detection helps identify unusual behaviors that can signal a threat, making it a valuable addition to modern security strategies.
What Is Anomaly Detection?
Anomaly detection is the process of identifying data patterns that differ significantly from normal behavior. In the cybersecurity field, anomalies—also known as outliers—are deviations from expected behavior or events in a network or system. Detecting these anomalies allows security teams to quickly identify unusual activities or patterns that may signal potential threats or ongoing cyberattacks.
Unlike traditional detection methods that rely on known attack signatures, anomaly detection leverages statistical models and machine learning to uncover abnormal behaviors — even when no known signature exists. This makes it a powerful tool in identifying sophisticated, novel, or insider threats that often go unnoticed by rule-based systems.
By integrating anomaly detection into a broader cybersecurity strategy, organizations can enhance their ability to detect advanced threats, including insider attacks and zero-day exploits. This proactive approach helps security teams quickly recognize and respond to potential risks, maintain system integrity, and protect sensitive data. As cyber threats become more complex, anomaly detection is no longer optional — it’s a critical component of modern threat detection and response.

Types of anomalies
Anomaly detection is the process of analyzing data sets to identify individual events or patterns that differ significantly from baseline, normal activity. In cybersecurity, these anomalies can be early warning signs of potential threats such as data breaches, cyber attacks, or system failures. By detecting anomalous behavior early, organizations can act quickly to limit risk, minimize potential damage, and speed up incident response and recovery.
There are three types of anomalies that can be detected by an anomaly detection system:
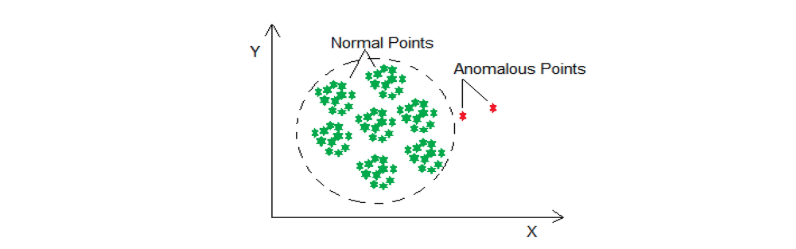
- Point anomalies: These occur when a single data point deviates significantly from the norm. For example, a sudden spike in login attempts or unexpected network traffic. Point anomalies are often early indicators of security breaches or unauthorized access and are among the most commonly detected anomalies in cybersecurity.
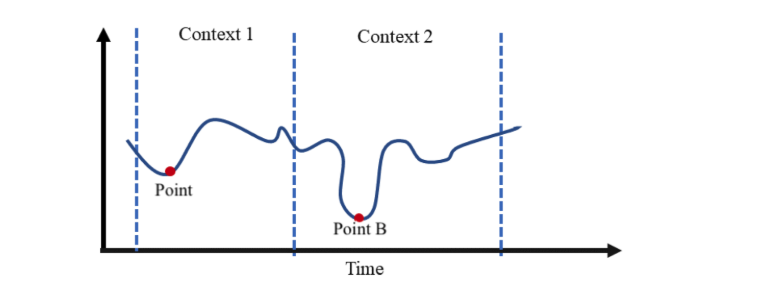
- Contextual anomalies: These are unusual behaviors that only appear abnormal within a specific context. For example, logging in from an unusual geographic location or outside normal business hours may indicate a contextual anomaly. Such anomalies often signal insider threats, compromised accounts, or unauthorized activity that might otherwise be missed by traditional rule-based detection.
- Collective anomalies occur when a group of related data points collectively deviates from normal behavior, even if the individual points appear benign. For example, a user cloning multiple repositories to their computer in a short period of time—especially when they’re about to leave their job—may indicate suspicious activity. While less common, these anomalies often signal more complex and organized threats that require immediate action.
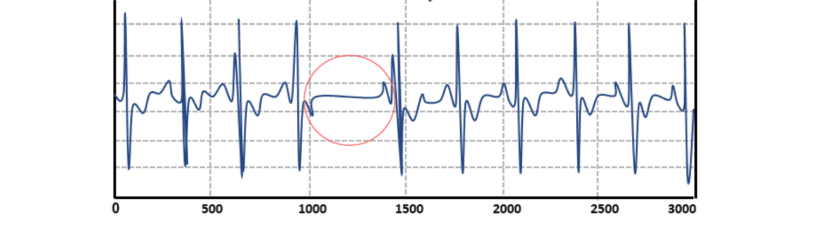
Modern anomaly detection systems use advanced techniques, including machine learning (ML), artificial intelligence (AI), and even deep learning algorithms, to quickly and accurately analyze massive volumes of data. These systems compare patterns against historical data, apply dynamic thresholds, and leverage neural networks to identify subtle or complex anomalies. Among the types of anomalies detected, point anomalies are the most common, but contextual and collective anomalies often indicate more significant and organized threats—making their accurate detection essential for effective security management.
How Anomaly Detection Works
Anomaly detection identifies deviations from established patterns of normal behavior, allowing organizations to spot unusual activity that may signal cyber threats. In cybersecurity, these anomalies can serve as early indicators of malicious actions such as malware execution, privilege escalation, or lateral movement across systems. Unlike static, rule-based systems, anomaly detection is dynamic continuously learning from historical data and adapting to the changing threat landscape.
Core Techniques Behind Anomaly Detection
The core of anomaly detection is the creation of behavioral baselines through the analysis of both historical data. This process relies heavily on advanced statistical methods and machine learning techniques:
- Feature extraction: Key behavioral indicators—such as login frequency, data transfer volume, or access patterns—are identified to determine what constitutes normal activity.
- Data modeling: Algorithms such as clustering, decision trees, and neural networks classify and analyze data, helping to distinguish between normal and suspicious behavior.
- Real-time monitoring: Incoming data streams are continuously evaluated against learned models to detect and alert on anomalies as they occur.
Detection Methods in Practice
Modern anomaly detection systems employ a variety of approaches to enhance accuracy and efficiency:
- Machine Learning-Based Detection: Unsupervised learning is effective at detecting hidden patterns and outliers in large, unlabeled data sets, while supervised learning uses labeled examples of past attacks to refine a system’s ability to recognize known threats.
- Behavioral Analytics: By continuously monitoring and learning from user and system behavior over time, these systems can detect subtle deviations that could signal insider threats or compromised accounts.
- Hybrid Modeling: Combining traditional rules-based logic with AI-driven analysis, hybrid approaches provide a balanced and adaptive solution—capable of identifying both established attack patterns and emerging, previously unknown threats.
Applications of anomaly detection
Anomaly detection is widely used in many areas of cybersecurity due to its ability to identify unusual behaviors that may indicate potential threats. Here are some common and impactful use cases:
Fraud Detection
In financial systems or e-commerce platforms, anomaly detection can identify unusual transactions such as purchases from unfamiliar geographic locations, unusually large amounts, or behavior inconsistent with a user’s history. This helps prevent financial fraud, credit card abuse, and unauthorized withdrawals.

For example, a user who typically makes small purchases suddenly makes multiple large transactions in a short period of time from overseas — the system flags this as potential fraud.
Unauthorized Access Detection
Anomaly detection helps detect unusual login activity, such as logging in at unusual times, from unexpected locations, or using unfamiliar devices.

For example, an office worker who usually logs in between 9am and 5pm suddenly logs in at 2am from a different country — this could be a sign of a compromised account.
Malware and Attack Detection
Anomaly detection can reveal suspicious behavior from internal users, such as mass file downloads, unauthorized data access, or attempts to steal sensitive information.
For example, an employee who is leaving the company copies multiple repositories to a personal device — the system flags this as a potential data leak.

Network Activity Monitoring
Network monitoring systems can use anomaly detection to identify unusual traffic flows, suspicious device-to-device communications, or unauthorized configuration changes.
For example, a server that normally only receives traffic suddenly starts initiating many outgoing requests — this could indicate that the server has been compromised.
Advantages of anomaly detection
Anomaly detection gives cybersecurity teams a proactive advantage by spotting anomalies that traditional rules-based systems may miss. Instead of relying only on known threat signatures, it learns patterns of normal behavior and detects deviations that may indicate malicious activity. This makes it especially effective against sophisticated threats such as zero-day exploits, insider attacks, and advanced persistent threats (APTs). With real-time analytics and adaptive learning, anomaly detection enhances an organization’s ability to respond quickly and build a more resilient security posture.

When integrated into a broader cybersecurity framework, anomaly detection helps organizations detect threats earlier in the attack lifecycle. It identifies suspicious activity that might otherwise go unnoticed—such as unusual user behavior or subtle lateral movement within the network. By detecting these signs early, security teams can stop threats before they escalate, minimizing potential damage and accelerating incident response and recovery. This early intervention is key to maintaining business continuity and minimizing operational disruption.
Beyond detection, anomaly detection also contributes to overall security effectiveness. It helps prioritize high-risk alerts, reduces false positives, and allows teams to focus their efforts where they matter most. Additionally, it provides actionable insights that improve decision-making and guide effective incident response strategies. In today’s ever-changing threat landscape, anomaly detection is not just an additional layer of protection, but a foundational element of any modern cybersecurity strategy.
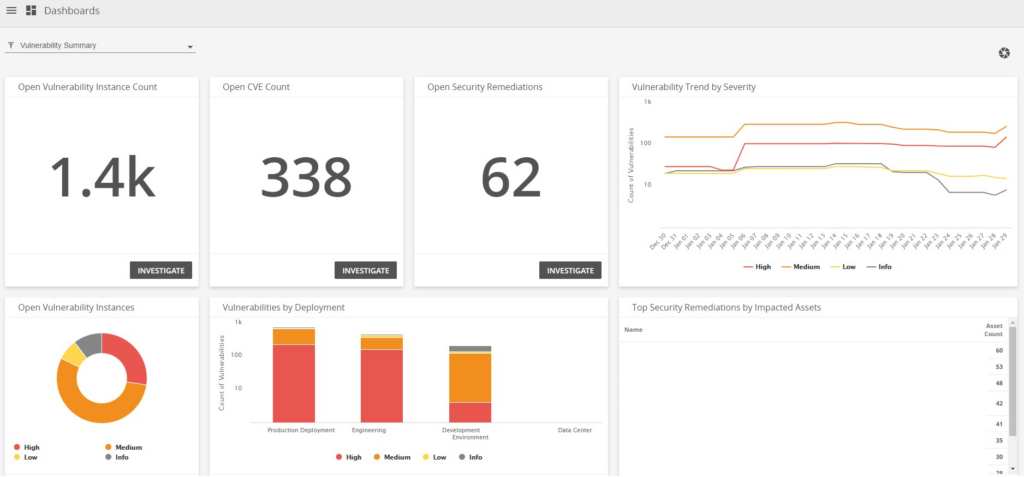
Challenges in anomaly detection
While anomaly detection is a powerful component of modern cybersecurity, implementing and maintaining it effectively presents several key challenges. These obstacles can impact the accuracy, efficiency, and reliability of detection systems—especially in large-scale, dynamic environments.
Accuracy and False Alerts
One of the biggest challenges is maintaining accuracy. Human behavior and system operations are complex and dynamic, making it difficult for even the most advanced models to establish a consistent baseline for what is “normal.” This can lead to false positives, where normal behavior is flagged as suspicious, overwhelming security teams and causing alert fatigue. Equally problematic are false negatives, where real threats go undetected—leaving the organization at risk of a breach. Inadvertent anomalies, such as legitimate but unusual behavior, can also skew model performance and skew detection accuracy.

Dependence on High-Quality Data
Anomaly detection systems are highly dependent on the quality, volume, and variety of data on which they are trained. Incomplete, noisy, or biased data can degrade model performance, leading to missed threats or excessive false alarms. Furthermore, changing environments—including changes in user behavior, system upgrades, or the addition of new assets—can shift baselines over time. Without continuous model tuning and retraining, detection accuracy can decline as the system becomes outdated or unsuitable for current operations.

Scale and Real-Time Processing
As organizations grow, so does the volume of data their systems generate. Processing large-scale, real-time data streams is a significant technical challenge that requires scalable infrastructure and high-end computing resources. Many cybersecurity environments involve multiple tools and systems that generate massive output data that must be aggregated, analyzed, and processed in a timely manner. Without robust data processing pipelines or distributed computing strategies, performance bottlenecks and detection delays can occur.
Interpretability and Response Readiness
Anomaly detection systems—especially those powered by complex machine learning or deep learning models—can sometimes act like “black boxes” flagging anomalies without a clear explanation. This lack of interpretability makes it difficult for analysts to understand the nature of the alert or determine an appropriate response. Without transparency or contextual understanding, even accurate alerts can lead to delayed or ineffective action.
Adversarial Attacks and Evolving Threats
As anomaly detection systems become more sophisticated, attackers are adapting. Adversarial machine learning techniques aim to manipulate training data or exploit weaknesses in models to avoid detection. Furthermore, the cyber threat landscape is constantly evolving, requiring models to continuously adapt and learn from new attack techniques, behaviors, and tactics. Static or outdated detection models risk becoming ineffective in the face of new threats.
Real World Case-Studies on Cyber Security
In this section, we will review a real-world case study in which a real-world security incident was detected using anomaly detection methods and explore how an organization responded to the threat.
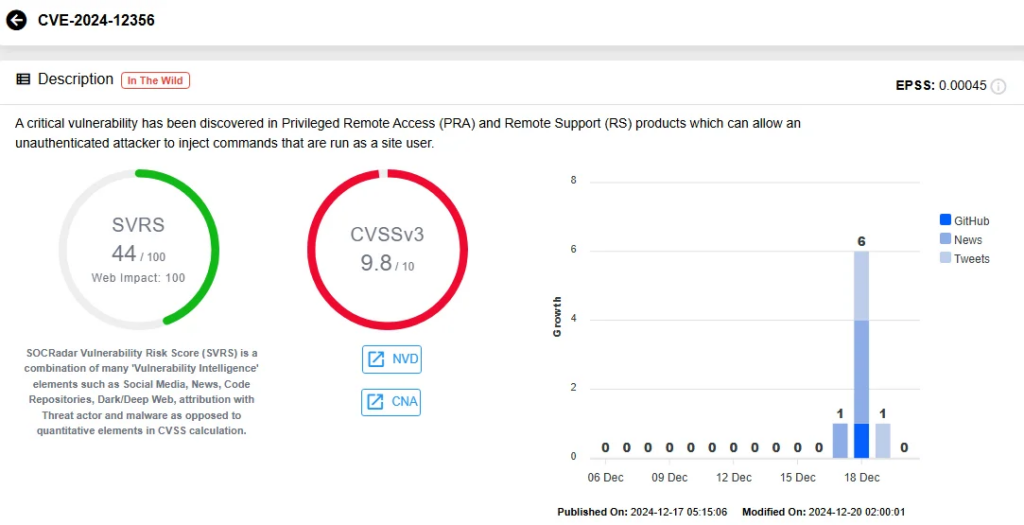
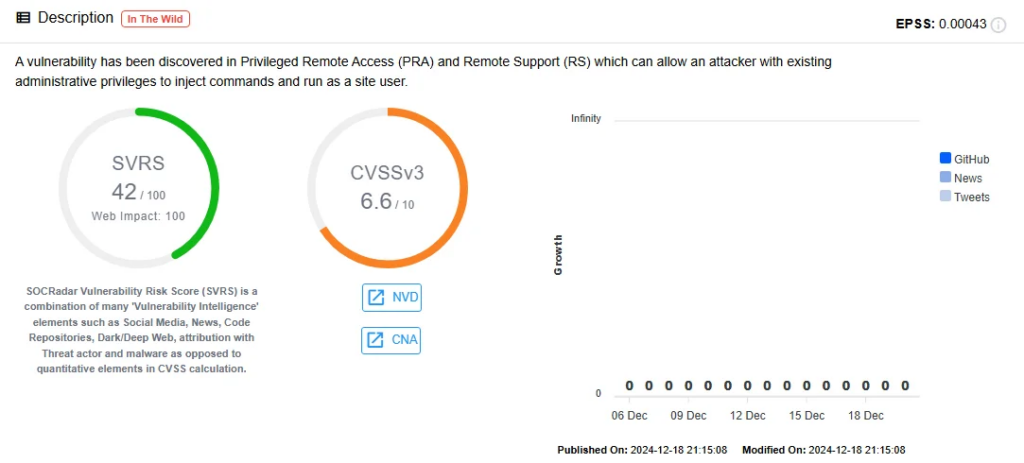
BeyondTrust, a company specializing in privileged access management solutions (Privileged Remote Access – PRA and Remote Support – RS), discovered two serious security vulnerabilities: CVE-2024-12356 (critical severity, CVSS 9.8) and CVE-2024-12686 (medium severity). CVE-2024-12356 allows unauthenticated attackers to execute arbitrary commands on the system via a command injection flaw, while CVE-2024-12686 enables attackers with admin privileges to upload malicious files and escalate privileges. Both vulnerabilities were exploited in the wild as zero-days and have been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.

The incident began on December 2, 2024, when BeyondTrust detected unusual activity in some of its Remote Support SaaS instances. By December 5, 2024, the company had identified a compromised API key that was used by an attacker to gain unauthorized access and reset account passwords. BeyondTrust patched the vulnerabilities for cloud customers between December 16 and 18, 2024, and also released fixes for on-premises deployments. The Cybersecurity and Infrastructure Security Agency (CISA) requires federal agencies to patch CVE-2024-12356 by December 27, 2024, and CVE-2024-12686 by February 3, 2025.
Incident Timeline and Response Summary
- December 2, 2024: BeyondTrust detected unusual activity in its Remote Support SaaS environment, signaling the beginning of the incident.
- December 5, 2024: Investigation revealed that a critical API key had been compromised, allowing attackers to reset account passwords and access systems without authentication.
- December 16–18, 2024: Patches were deployed for cloud (SaaS) customers to address the critical vulnerability CVE-2024-12356.
- After December 18, 2024: On-premise patches were released for self-managed customers, who were responsible for applying updates themselves.
- December 27, 2024: CISA set a deadline for federal agencies to patch CVE-2024-12356 due to its high severity.
- February 3, 2025: CISA set a separate deadline to patch CVE-2024-12686, reflecting its lower severity level.
Detection and Initial Response
The incident was initially detected through BeyondTrust’s monitoring system, which identified anomalies within the Remote Support SaaS platform. Three days later, the root cause was traced to a compromised API key. The attacker used it to reset account passwords and gain unauthorized access, indicating weaknesses in credential management.
Upon discovery, BeyondTrust likely revoked the compromised key and began analyzing the attack. Two vulnerabilities were identified: CVE-2024-12356 (unauthenticated command injection) and CVE-2024-12686 (privilege escalation via malicious file upload).
Mitigation and Investigation
From December 16–18, patches were rolled out to cloud customers to address the most severe vulnerability. A separate patch for CVE-2024-12686 was also released, though it required admin access to exploit. For on-premise deployments, BeyondTrust provided update packages with urgent upgrade recommendations.
BeyondTrust also engaged external security experts to assist in a deeper forensic investigation. The incident gained broader attention after being linked to an attack on the U.S. Treasury, attributed to the China-based threat group Silk Typhoon.
Recommendations and Impact
Customers were strongly advised to update their systems immediately and strengthen API key management practices. The incident had reputation consequences for BeyondTrust, as it exposed serious security gaps in their own security products—highlighting the importance of continuous monitoring, rapid response, and secure credential handling in privileged access solutions.
Lessons learned
The BeyondTrust incident clearly demonstrates the critical role that anomaly detection plays in modern cybersecurity. Early identification of anomalous activity on December 2, 2024, allowed security teams to begin investigating and containment before attackers could cause more widespread damage. Without timely detection of behavioral anomalies—such as unauthorized access patterns or unusual password resets—the breach may have gone unnoticed for much longer. This case reinforces the value of proactive monitoring and anomaly-based detection methods as essential tools for reducing response times, limiting impact, and detecting sophisticated, stealthy attacks before they escalate.
Inclusion
As cyber threats become more sophisticated and difficult to detect, anomaly detection has become an essential part of modern cybersecurity strategies. By identifying unusual behavior and deviations from normal patterns, it allows organizations to uncover potential risks, respond to emerging threats in real time, and reduce the likelihood of security incidents slipping through the cracks. From detecting fraud and insider threats to detecting malware and unauthorized access, anomaly detection provides the visibility and intelligence needed to stay ahead of attackers.
While challenges like data quality, false positives, and scalability remain, continued advances in AI and machine learning are making anomaly detection more accurate, adaptive, and practical than ever. When implemented thoughtfully and integrated with other security tools, anomaly detection not only enhances protection but also it empowers security teams to act faster, smarter, and more confidently in the face of evolving threats.
Therefore, when combined with rules-based detection systems, anomaly detection provides a more powerful and effective approach to cybersecurity. While rules-based approaches are great for identifying known and well-defined threats, anomaly detection fills the gaps by detecting sophisticated or previously unseen malicious behavior. Together, they create a comprehensive layer of defense – allowing organizations to not only respond to existing threats, but also proactively detect and block sophisticated and emerging attacks.
Reference
[1] https://www.darktrace.com/cyber-ai-glossary/anomaly-detection
[2] https://www.crowdstrike.com/en-us/cybersecurity-101/next-gen-siem/anomaly-detection
[3] https://aws.amazon.com/what-is/anomaly-detection/
[4] https://socradar.io/beyondtrust-security-incident-command-injection/
[5] https://www.cve.org/
[6] https://www.securityweek.com/beyondtrust-patches-critical-vulnerability-discovered-during-security-incident-probe/