Today, AI has advanced rapidly, bringing numerous benefits to the development of modern society with applications spanning various fields. Behind this success lies Deep Learning, a sub-branch of AI, which has driven technological breakthroughs and revolutionized how machines learn and adapt. Deep Learning, with its ability to utilize deep neural networks, has made it possible for AI to analyze massive datasets, recognize patterns, and make predictions with unprecedented accuracy. This breakthrough has paved the way for innovations in healthcare, finance, transportation, and countless other industries, transforming the way we live and work.
However, stepping into the realm of Security — a discipline characterized by rigor and high demands for precision — Deep Learning faces significant challenges in finding harmony. Although AI and Security are often regarded as a “perfect pair” for building robust defenses for systems and data, AI’s “golden child” — Deep Learning — has yet to establish a sustainable relationship with Security.
This article is also published on the https://nika.ai3sec.com/deep-learning-and-security-a-meeting-without-staying-391b4fdb5f97

What makes Deep Learning, such an extraordinary technology, struggle to collaborate effectively with Security? And is there a way to unlock the full potential of this partnership? The answers are not straightforward, but this is undoubtedly a fascinating story worth exploring!
Let’s Explore the Foundations
Before diving deeper, let’s take a moment to understand what Deep Learning is, how it works, and how it might support the needs of Security.
Deep Learning: is a subset of Machine Learning that utilizes multi-layered neural networks, called deep neural networks, to simulate the brain’s ability to make complex decisions. This allows Deep Learning to analyze large datasets, identify patterns, and learn from past experiences to make predictions and decisions. Its strength lies in its capability to process vast and complex data, which makes it a promising tool for tackling modern technological challenges.
Security: focuses on protecting data and systems from threats such as unauthorized access, system attacks, and data theft. To achieve this, an effective attack detection model is essential, and alerts must be sent to the system promptly in real-time. This ensures the fastest possible detection of anomalies within the system, allowing for timely responses to ongoing issues.

What Security Needs
The primary requirement of Security is the ability to detect attacks and anomalies within the system. Once an issue is identified, alerts are generated and sent to a Security Information and Event Management (SIEM) system, where security analysts review the alerts and decide whether to take further action or dismiss them.
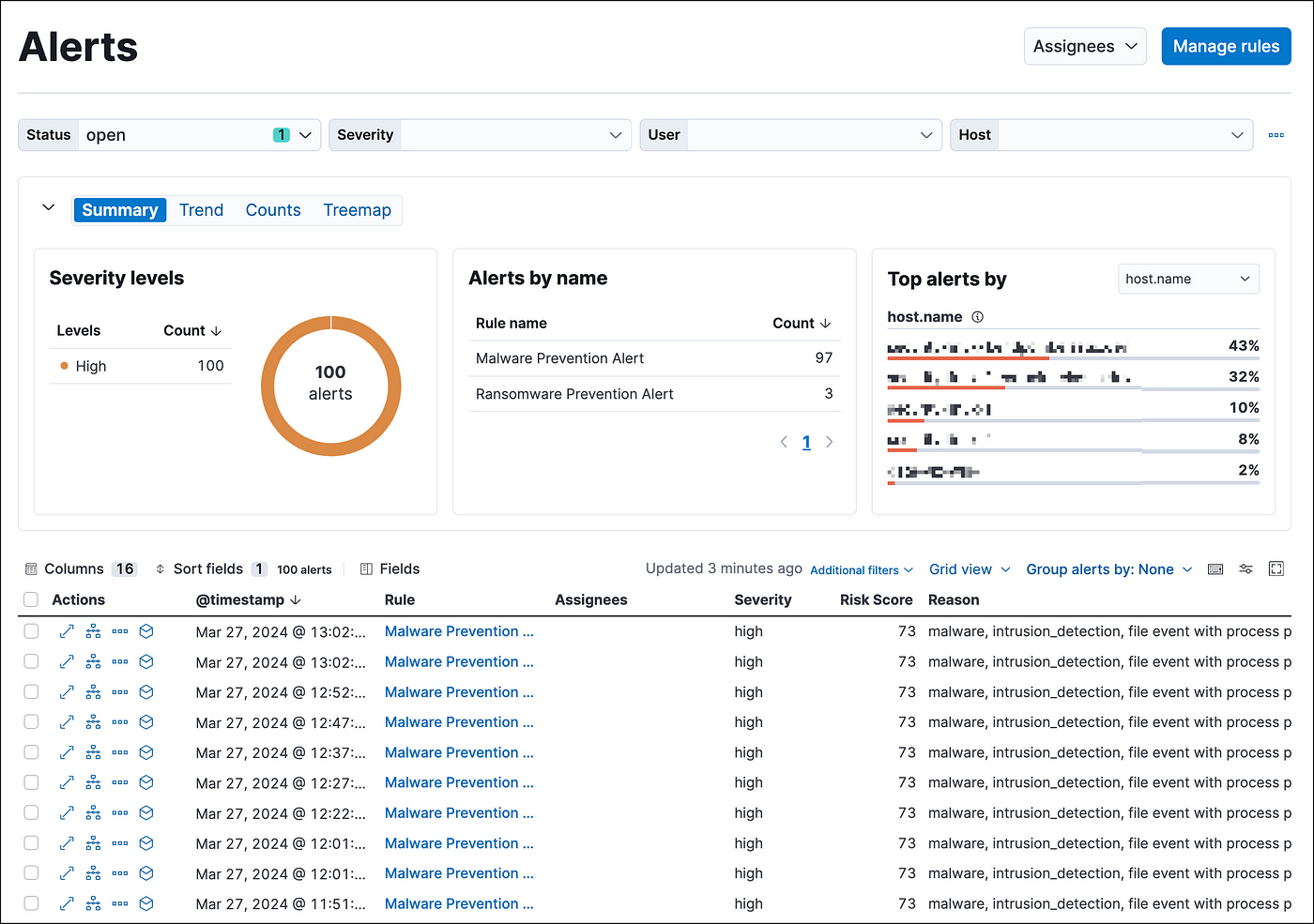
When analyzing an alert, analysts ask critical questions such as: what is this alert about, where did this alert originate, when did it occur … And most importantly: Why did this alert happen?
For instance, if you receive an alert about an unusual login to your Facebook or Gmail account, the first question you ask is: Why did this alert occur? Maybe it’s because a new device was detected, or you logged in from a new location. This context helps you verify whether the action was yours. However, if you receive a vague alert simply stating “unusual login detected” without any specific details, it leaves you confused and concerned about whether your account has been compromised.
This highlights the importance of providing clear reasons behind an alert, as it helps security analysts quickly identify the cause and make accurate decisions.
One crucial aspect of Security is the need for speed and efficiency within a short timeframe. Implementing a monitoring and surveillance system must be done as quickly as possible to ensure the system is actively safeguarded and potential threats are promptly detected. Delays in deployment can leave systems vulnerable, making it essential for security solutions to prioritize rapid implementation while maintaining reliability and effectiveness. The quicker the system is up and running, the sooner it can provide the necessary protection to maintain operational integrity.
Can Deep Learning Meet These Needs?
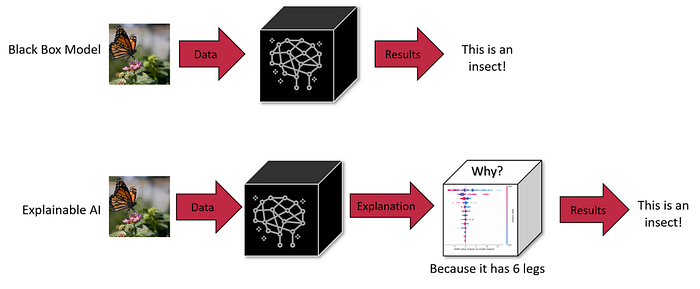
One of the significant challenges with Deep Learning is its inability to explain why it flagged an alert — lack of explainability. Often referred to as a “black box”, Deep Learning can indicate whether there is an anomaly or an attack, but it struggles to provide clear reasons or explanations (Explainable AI). This lack of transparency makes handling alerts more resource-intensive and time-consuming for security teams.
Another issue is the sheer volume of alerts generated — overwhelming number of alerts. Let’s assume a Deep Learning model operates with 90% accuracy. If there are 100 alerts, 90 will be accurate, but 10 will be false positives. While this might seem manageable, consider a scenario where the system processes 100,000 logs. With the same accuracy rate, it would generate 10,000 false alerts, overwhelming security analysts and making it nearly impossible to review all the alerts effectively.
Moreover, implementing Deep Learning on an infrastructure requires significant resources in both technology and human expertise. From data collection and processing to model training and deployment, the process is resource-intensive — Resource Issue. In security, applying detection to a new log must happen swiftly to ensure the system remains secure. However, Deep Learning often requires considerable time for analysis, training, and fine-tuning the model compared to traditional rule-based detection methods tailored to specific log sources.
Deep Learning often performs best when using pre-trained models as a starting point. However, in the field of Security, creating such pre-trained models is extremely challenging due to the lack of standardized data and the unique nature of each organization’s systems — lack of pre-trained models for security. This makes it difficult to develop a model that can generalize effectively across different businesses and adapt to their specific requirements.
Understanding the insights and results produced by Deep Learning models requires significant expertise, which can be a resource-intensive task for cybersecurity analysts — Knowledge Gap. Unlike traditional tools that provide straightforward outputs, Deep Learning often presents complex, nuanced findings that demand time and effort to interpret. For instance, when a Deep Learning model flags an anomaly, the lack of clear reasoning or explainability behind the alert can leave security professionals scrambling to decipher the underlying cause. This not only delays response times but also diverts valuable resources from addressing other critical tasks. In high-pressure environments where quick and accurate decisions are paramount, the intricate nature of Deep Learning can become a bottleneck rather than a facilitator.

Why Are Deep Learning and Security Struggling to Connect?
Security, with accustomed to transparent and actionable tools, often finds it challenging to embrace the complexity and lack of explainability that comes with Deep Learning. This “black box” nature makes it difficult for cybersecurity professionals to fully grasp the insights and results that Deep Learning provides, creating a gap in trust and usability. At the same time, Deep Learning systems, designed to adapt and evolve, often clash with the rigid and structured processes of traditional security systems, making integration a daunting task.
Moreover, Security demands solutions that are not only accurate but also quick and easy to interpret. While Deep Learning is undoubtedly powerful, its inability to deliver immediate results or clear explanations can hinder its effectiveness in addressing urgent threats. This disconnect reduces the agility and efficiency needed in critical security operations, leaving a gap that needs to be bridged.
The Future: Will They Stay Together?
Although the relationship between Deep Learning and Security still has significant gaps, it does not mean they cannot advance further in the future. To achieve a sustainable and synergistic connection, both sides need to evolve in multiple aspects.
DL models must offer clearer explanations for their decisions, narrowing the trust gap with Security teams and enabling easier understanding of DL’s outcomes. Simultaneously, improving accuracy and reducing the burden of alerts is crucial for Security to enhance its effectiveness in safeguarding data and systems. Moreover, combining DL with traditional rule-based security systems would create a multi-layered defense that is both flexible and reliable.

To maintain efficiency, DL must adopt active learning by continuously updating with new data to counter evolving attacks. Additionally, optimizing resource utilization, deployment, and operations will be essential to meet Security’s demands for quick responses and robust data protection. These advancements will not only bridge the gap between DL and Security but also pave the way for a promising future of collaboration between these two critical fields.
Conclusion
Deep Learning and Security are like two puzzle pieces that are almost fitting but require fine-tuning to align perfectly. Without this adjustment, they remain merely a fleeting encounter without a lasting bond. Their meeting is not coincidental, it underscores the growing need for smarter, more adaptive solutions in cybersecurity. However, until the challenges of trust, data, and integration are fully addressed, this relationship might remain just a passing interaction.
The future, holds great promise. With advancements in explainable artificial intelligence and stronger data practices, we may witness the day when Deep Learning and Security are no longer distant but instead forge a lasting and harmonious partnership, much like the vision of Artificial Intelligence and Security: A Predestined Partnership.
Reference
[1] The dangers of trusting black-box machine learning- https://bdtechtalks.com/2020/07/27/black-box-ai-models/
[2] What is deep learning? — https://www.ibm.com/topics/deep-learning
[3] Information Security: The Ultimate Guide — https://www.imperva.com/learn/data-security/information-security-infosec
[4] What is explainable AI? — https://www.ibm.com/topics/explainable-ai
[5] Understanding and fighting alert fatigue — https://www.atlassian.com/incident-management/on-call/alert-fatigue
[6] Challenges in Deep Learning — https://www.geeksforgeeks.org/challenges-in-deep-learning/#top-deep-learning-challenges
[7] G. Xu, H. Li, H. Ren, K. Yang and R. H. Deng, “Data Security Issues in Deep Learning: Attacks, Countermeasures, and Opportunities,” in IEEE Communications Magazine, vol. 57, no. 11, pp. 116–122, November 2019, doi: 10.1109/MCOM.001.1900091.
[8] Artificial Intelligence and Security: A Predestined Partnership — https://blog.ai3sec.com/artificial-intelligence-and-security-a-predestined-partnership-9a244b322c29
